How to Join RHEL 8 to Windows Active Directory Domain Service
How to Join Redhat 7/Redhat 8/Redhat 9/CentOS 7/CentOS 8 to Windows Active Directory Domain Service
Authenticate a Linux operating system with centralize domain
controller means Window Server base active directory domain services, it is a
best practice to manage operating system administrative and operation task. With
this centralized authentication no need to create user on Linux operating
system, for any kind of administrative task user will add on file “sudoers”,
they will perform administrative or operation base task as per the
authorizations to execute all commands or execute specific commands. In this
scenario authenticate means user id and its password centrally manage by active
directory domain service that can be on windows server 2012 R2/2016/2019/2022,
and authorization means provides a rights that user will execute all commands
or specific commands with sudo rights. Port for ldap communication is use
389/tcp for security (LDAPS) port 636/tcp is use and for DNS port is use
53/udp.
realmd: In Linux realmd is use for authentication and
domain membership with the use of sssd, realmd is a Linux system service.
oddjob: oddjob is a Linux service that is system wide message bus is
also known as D-Bus system bus. This daemon is use as a helper process for
authorization and provide support of application that require privileged
operation to perform.
oddjob-mkhomedir: This daemon in Linux is a oddjob helper that is use to
create the home directories of user.
sssd: sssd stands for System Security Service Daemon, this daemon in
Linux is use to access the remote directories and authentication mechanism. In
System Security Service Daemon (sssd) file both ldap and ldaps (Certificate
based) configuration are perform.
adcli: In Linux, adcli is a daemon that is use to join a Linux machine with
active directory domain.
krb5-workstation: This is a Kerberos
package for workstation (Linux machine). The krb5-workstation contains the
basic Kerberos programs (kinit, klist,kpasswd, kdestroy), for Kerberos base
authentication in a domain environment of windows active directory the package
“krb5-workstation” must require.
samba-common-tools: The package “samba-common-tools” is use to allow
client machine to communication over SMB/CIFS protocol in domain base
environment.
sssd-tools: The sssd-tools package is use with the System Security
Service Daemon (sssd).
To install the packages for authenticate Redhat 7/Redhat
8/Redhat 9/CentOS 7/CentOS 8 with Lightweight directory access protocol (LDAP)
means Active Directory Domain Services of Windows Server, type the below
mention command.
yum install realmd oddjob oddjob-mkhomedir sssd adcli krb5-workstation samba-common-tools sssd-tools -y
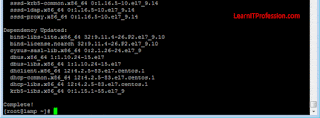
The packages has been successfully installed on Redhat
7/Redhat 8/Redhat 9/CentOS 7/CentOS 8, as shown in below mention image. The all packages are available on their respective repository means CentOS platform automatically connect their repository through internet and for RedHat enterprise Linux (RHEL) you need to first create a local repository server through redhat subscription.
For IP (Internet Protocol) and DNS (Domain Name Server) configuration
on Redhat 7/Redhat 8/Redhat 9/CentOS 7/CentOS 8, type the below mention
command. By use of this command you can also set the hostname of the machine but you can also set the hostname by use of command "hostname set-hostname abc", here "abc" is the hostname.
nmtui
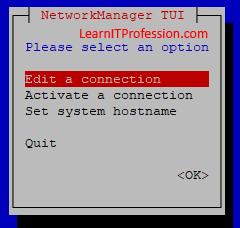
Select “Edit a connection” on Network Manager Text User
Interface (TUI) then press enter. Here you can also set a hostname through Graphical User Interface (GUI) and through Activate a connection you can activate or deactivate the network interface, here we have only single interface therefore do not deactivate it otherwise you will not able access Linux machine through network by use of putty software means you cannot access the Linux machine by use of ssh (secure shell) on port 22.
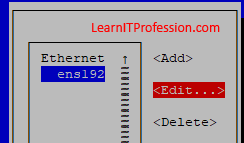
Select Ethernet interface "ens192" then press “tab” to “Edit” the
network interface configuration. Here you can also add multiple network interface, but first you need to add the network interface with the virtual machine or physical machine.
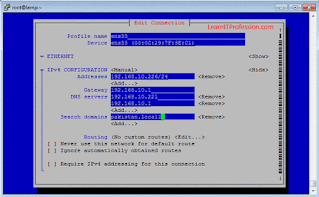
Provide IP (Internet Protocol) address with subnet address and gateway, also provide a name server address and domain name as per the environment shown in below image. Here you can also disable IPv6 address if you no need to require it, we have configure ipv6 address in ignore mode.
Select “OK” to save the IP (Internet Protocol) address, name server address and domain name configurations as shown in the below image. In image you can see that automatically connect option should be select otherwise Ethernet interface connectivity will not work.
After “quit” from the Network Manager Text User Interface (TUI), for restart and check the status of network service type the below mention commands. This command is use for Redhat Enterprise Linux 8 (RHEL) and Redhat Enterprise Linux 9 (RHEL).
systemctl restart NetworkManager.servicesystemctl status NetworkManager.service
On Redhat Enterprise Linux 7 (RHEL) for restart and check the status of network service type the below mention commands.
systemctl restart networksystemctl status network
To verify the name server and Domain Name entry available on file
“resolv.conf”, type the below mention command to view only the configuration that have set above by use of the command "nmtui".
cat /etc/resolv.conf
Configure the SElinux in disable or permissive mode, use
editor vi to modify file “/etc/selinux/config”.
It is a best practice to configure SElinux in permissive mode rather than
disable because in permissive mode SELinux create warning, you can say it a logs that update you about a security issues due to this you can debug and troubleshoot the issues.
vi /etc/selinux/config
Finally join the Linux base operating system “Redhat
7/Redhat 8/Redhat 9/CentOS 7/CentOS 8” with Active Directory Domain Services
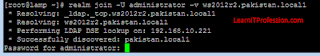
(ADDS), type the below mention command. The command "realm" is use to authenticate a Linux machine in domain environment.
realm join -U username -v FQDNrealm join -U administrator -v ws2012r2.pakistan.local1
The Linux base operating system “Redhat 7/Redhat 8/Redhat
9/CentOS 7/CentOS 8” has been successfully authenticate with Active Directory
Domain Services (ADDS), In this environment domain name “pakistan.local1”.
To give domain user “administrator” complete administrative
rights means root level privileged modify file “/etc/sudoers”, type the below mention
command.
visudo
Add below mention line at the end of file to give domain user "administrator" complete administrative rights to execute all the commands with sudo.
administrator ALL=( ALL) ALL
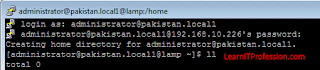
Login with domain user “administrator” on Linux machine “Redhat 7/Redhat 8/Redhat 9/CentOS 7/CentOS 8” to verify that domain user is authenticate in a domain environment.
In the above image you can see that domain user "administrator" is login by
use of fully qualified domain name, if you want that domain user login with name only
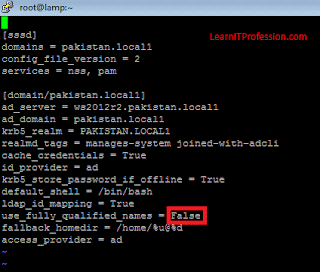
modify file “sssd.conf”.
vi /etc/sssd/sssd.conf
Modify,
Use_fully_qualified_names = False
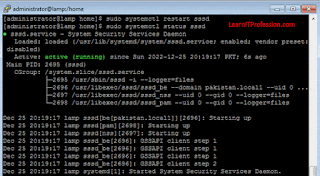
After modify file “/etc/sssd/sssd.conf” must restart sssd service. To
restart and check the status of sssd service type the below mention commands.
sudo systemctl restart sssdsudo systemctl status sssd

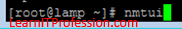




Comments
Post a Comment