How to Configure SSL Certificate with Certificate Template on Redhat 8 by ADCS
How to Configure SSL Certificate for Apache Web Server with and without Certificate Template on Redhat 9/Redhat 8/Redhat 7/CentOS 8/Centos 7 by Active Directory Certificate Service
Secure Socket Layer (SSL) is a security protocol that is
also called as a encrypted security protocol, Secure Socket Layer (SSL) encrypt
the traffic from plain text to a cipher text that secure the entire traffic from
server to client machine that websites access from the web browser. Due to the
encryption the data is save from the attacker. Secure Socket Layer (SSL) final
version is 3.0 and the transport layer security (TLS) replace Secure Socket
Layer (SSL) which latest version is TLS 1.3 to the transport layer security
(TLS) family.
Secure Socket Layer (SSL) protect the user privacy by
encrypting the data between the browser and user client machine. The Secure Socket
Layer (SSL) first time introduce since 1994 that have a version 1.0 but this version
was not release due to security issues, the next version of Secure Socket Layer
(SSL) was release in 1995 that have a version 2.0 and the final version 3.0 of
Secure Socket Layer (SSL) was released in 1996. The Secure Socket Layer (SSL)
prevent the cyber-attacks in the era of 1995 to 1999 but due to security flaws
Secure Socket Layer (SSL) v 3.0 upgrade to Transport Layer Security (TLS) that
was first introduced in 1999 and it version is 1.0, then Transport Layer
Security (TLS) upgrade to version 1.1 in 2006. The version 1.1 of Transport
Layer Security (TLS) have an additional feature to prevent Cipher block
Channing attack. The Transport Layer Security (TLS) has released version 1.2 in
2008 with addition of Advance Encryption Algorithm cipher suites (AES use the
same keys for encryption and decryption) and removing the Data Encryption
Standard (DES use 56-bit key size to encrypt 64-bit plain text into 64-bit
cipher text). The latest version of Transport Layer Security (TLS) v1.3 has
been develop in 2018 that support the entire latest browsers, Transport Layer
Security (TLS) v1.3 remove old obsolete cryptographic algorithm (SHA1, MD5,
etc.) and enhance the security of older cryptographic algorithm.
Types of SSL Certificate: There are three types of
Secure Socket Layer (SSL) Certificate; Organization Validated (OV SSL),
Extended Validation (EV SSL) and Domain Validated (DV SSL) and the all three
Secure Socket Layer (SSL) Certificate have same level of encryption.
How SSL Works: Two types of cryptography Secure
Socket Layer (SSL) are used symmetric cryptography and asymmetric cryptography.
In symmetric cryptography (encryption) single key (secret key) is use to
encrypt or decrypt the data, single secret key cannot be use for digital
signing. In asymmetric cryptography private and public key are used to encrypt
and decrypt the data respectively, it can be used for digital signing.
SSL Encryption: Secure Socket Layer (SSL) certificate
apply on a websites, technically Secure Socket Layer (SSL) certificate is a
Transport Layer Security (TLS) Certificate. Secure Socket Layer (SSL) are use
two types of encryption techniques, Public key cryptography standard (PKCS) and
Data Encryption Standard (DES)/triple Data Encryption Standard (3DES). In Public
key cryptography standard (PKCS) certificate encrypt and decrypt by use of
private and public key during the Secure Socket Layer (SSL) handshake. In Data
Encryption Standard (DES) is symmetric encryption algorithm that is use 64 bit
key, In 64bit key 8 bit are reserve for other purpose therefore it is actual
use 56 bit key (same key) for encryption and decryption the data.
Algorithm: Secure Socket Layer (SSL) use Key Exchange
Algorithm (RSA (Rivest–Shamir–Adleman),ECDH (Elliptic-curve Diffie-Hellman),
etc) that uses asymmetric encryption for authentication and for data encryption
symmetric encryption is use. Secure Socket Layer (SSL) use Bulk encryption
algorithm ((AES (Advanced Encryption Standard), 3DES (Triple Data Encryption
Standard), etc)) for data encryption. Secure Socket Layer (SSL) use RSA
(Rivest–Shamir–Adleman) and DSA (digital signing algorithm) for Digital
Signature or authentication algorithm. SSL/TLS use hash algorithm to protect
the integrity of message, the mode widely use hash algorithm that is Secure
Hash Algorithm (SHA256 and SHA512).
Create
SSL Certificate:
For the create Secure Socket Layer (SSL) certificate, first
need to create Certificate Signing Request (CSR) “apache1.csr” with key file
“apache1.key”. Here we are using RSA (Rivest–Shamir–Adleman) algorithm with key
length 2048 for secure data transmission, RSA (Rivest–Shamir–Adleman) algorithm
use public and private key for data encryption because it is type of asymmetric
encryption.
openssl req -new -newkey rsa:2048 -nodes -keyout apache1.key -out apache1.csr
Provide the below mention details as per the requirement
during the creation of Certificate Signing Request (CSR).
Country Name (2 letter code) [XX]:PKState or Province Name (full name) []:SindhLocality Name (eg, city) [Default City]:KarachiOrganization Name (eg, company) [Default Company Ltd]:ITOrganizational Unit Name (eg, section) []:SystemCommon Name (eg, your name or your server's hostname) []:apache1Email Address []:owais@abc.org.pkA challenge password []:An optional company name []:ITD
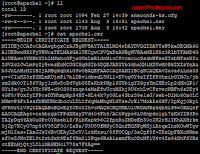
To list the content use command “ll” and copy the entire
content of Certificate Signing Request (CSR) use command “cat”, the command
“cat” is use for view the content of file then you easily copy the content from
“-----BEGIN CERTIFICATE REQUEST----” to “-----END CERTIFICATE REQUEST-----”
llcat apache1.csr
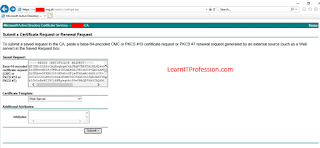
Here we are using Certificate Authority (CA) of Microsoft
that is Active Directory Certificate Service, put the entire content of Certificate
Signing Request (CSR) from “-----BEGIN CERTIFICATE REQUEST----” to “-----END
CERTIFICATE REQUEST-----” on “Base-64-encoded certificate request (CMC or PKCS
#10 or PKCS #7)” window and select certificate template “Web Server” then click
on “Submit”.
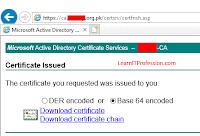
Move the Certificate Signing Request “CSR” file, key and downloaded
certificate file to the directory location “/etc/pki/tls/certs”. You can place
the key and downloaded certificate file to any location but need to define path
in file “ssl.conf” for main apache web server and for Virtual hosting you can
define Secure Socket Layer (SSL) certificate path and key path on Virtual Host
configuration file only.
mv apache1.csr /etc/pki/tls/certs/mv apache1.key /etc/pki/tls/certs/
Here we are using WinSCP to move downloaded Certificate “apache1.cer” from local host to web server directory path “/etc/pki/tls/certs/” on redhat 8 linux machine.
Install SSL Module: Web server on RHEL 9/RHEL 8/RHEL
7/CentOS 8/CentOS 7 use Secure Socket Layer (SSL) certificate that require
installation of Secure Socket Layer (SSL) module, to install the Secure Socket
Layer (SSL) module type the below mention command.
yum install mod_ssl.x86_64 -y
The Secure Socket Layer (SSL) module has been successfully installed on Red Hat Enterprise Linux 8 machine.
To modify Virtual Host configuration file of main domain go
to the directory location “/etc/httpd/conf.d/” by use of command “cd”, for list
the content use command “ll”, for rename the virtual host configuration file
use command “mv”. To modify/edit the file “owais.conf” virtual host
configuration of main domain use editor “vi”.
cd /etc/httpd/conf.d/llmv owais.conf owais.conf-4Aug2023vi owais.conf
Add the below mention code in virtual host configuration
main domain file “owais.conf”, in this virtual host configuration file
“owais.conf” website forward from port “80” to port “443”.
<VirtualHost apache1:80>Redirect permanent / https://apache1/</VirtualHost><VirtualHost apache1:443>SSLEngine on#Define SSL Protocol and SSL Cipher SuiteSSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 +TLSv1.3SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5:!3DESSSLHonorCipherOrder on#For website “apache1” web server certificate file pathSSLCertificateFile /etc/pki/tls/certs/apache1.cer#For website “apache1” web server private keySSLCertificateKeyFile /etc/pki/tls/certs/apache1.key#Enable Client AuthenticationSSLVerifyClient none#Provide Certificate Authority Certificate File PathSSLCACertificateFile /etc/pki/tls/certs/CA.cerSetEnv APP_ENV "OWAIS"ServerAdmin owais@abc.org.pkDocumentRoot /var/www/html/ServerName apache1DirectoryIndex index.htmlErrorLog logs/apache1-error_logCustomLog logs/apache1-access_log common<Directory "/var/www/html/">Options -Indexes +FollowSymlinksAllowOverride allRequire all granted</Directory></VirtualHost>
Above configuration of the virtual host file “owais.conf” is for the primary website due to it diversion from “http (port 80)” to “https (Port 443)”, in this virtual host configuration file “owais.conf” we have define SSL Certificate File Path, SSL Certificate Key File Path and Certificate Authority File Path. For Primary website you must define SSL Certificate File Path and SSL Certificate Key File Path on file “ssl.conf” that have directory location “/etc/httpd/conf.d/ssl.conf”.
To provide the Certificate
and it’s key file path on file “ssl.conf”, type the below mention command.
vi /etc/httpd/conf.d/ssl.conf
To provide SSL Certificate File path go to line number “85”
and provide SSL Certificate File path as mention below.
SSLCertificateFile /etc/pki/tls/certs/apache1.cer
To provide SSL certificate Key File path go to line number
“93” and provide SSL Certificate Key File path as mention below.
SSLCertificateKeyFile /etc/pki/tls/certs/apache1.key
After modification of virtual host configuration file
“owais.conf” and modification of Secure Socket Layer File “ssl.con” restart the
apache web server service ”httpd”, type the below mention command.
systemctl restart httpd
To verify website apache web server of virtual host
configuration “owais.conf” is successfully working with Secure Socket Layer
“SSL”, type the below mention Uniform Resource Locator “URL” on web browser.
Note: In a domain environment must create a host entry
“apache1” on Domain Name Server otherwise add hostname/website name with server
IP on host file of each client machine where you want to access website.
https://apache1/
To modify or create the Virtual Host Configuration file “malir.conf”
that is another domain, type the below mention command.
vi malir.conf
Add the below mention configuration on virtual host
configuration file “malir.conf”, this virtual host configuration is for Secure
Socket Layer (SSL) base website that run on “https, port 443”only. This is
customize virtual host configuration nor use default path of website and
neither use default path for logs.
#Virtual domain<VirtualHost malir:443>SSLEngine on#Define SSL Protocol and SSL Cipher SuiteSSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 +TLSv1.3SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5:!3DESSSLHonorCipherOrder on#For website “malir” web server certificate file pathSSLCertificateFile /etc/pki/tls/certs/malir.cer#For website “malir” web server private keySSLCertificateKeyFile /etc/pki/tls/certs/malir.key#Enable Client AuthenticationSSLVerifyClient none#Provide Certificate Authority Certificate File PathSSLCACertificateFile /etc/pki/tls/certs/CA.cerServerAdmin owais@abc.org.pkServerName malir.abc.org.pkDocumentRoot /owais/DirectoryIndex index.htmlLogLevel warnErrorLog /owais/logs/malir/error.logCustomLog /owais/logs/malir/access.log combined<Directory "/owais/">Options -Indexes +FollowSymlinksAllowOverride allRequire all granted</Directory></VirtualHost>
https://malir/
Create
Certificate By use of template for Red Hat Linux:
To create a certificate by use of Certificate Template first
create a Certificate Template file “openssl-san.cnf” or “abc.cnf”, actually if
you generate a Certificate Signing Request (CSR) With Certificate Template, in
browser error “NET::ERR_CERT_COMMON_NAME_INVALID”
will resolve and client machine will trust the server certificate because in
Certificate Template you have define Subject Alt Name. The Subject Alternative
Name is a way to define Trusted Domain Names and IP (Internet Protocol)
addresses for certificate.
To modify Certificate Template file “openssl-san.cnf”, type
the below mention command.
vi openssl-san.cnf
Add the below mention configuration in Certificate Template
file “openssl-san.cnf”.
[ req ]default_bits = 2048distinguished_name = req_distinguished_namereq_extensions = req_ext[ req_distinguished_name ]countryName = PKstateOrProvinceName = SindhlocalityName = KarachiorganizationName = OwaiscommonName = apache.abc.org.pk# Optionally, specify some defaults.countryName_default = [Pakistan]stateOrProvinceName_default = [Sindh]localityName_default = [Karachi]0.organizationName_default = [ITD]organizationalUnitName_default = [IT]emailAddress_default = [owais@abc.org.pk][ req_ext ]subjectAltName = @alt_names[alt_names]DNS.1 = apache1.abc.org.pkDNS.2 = apache1
openssl req -newkey rsa:2048 -nodes -sha256 -keyout apache1.key -out apache1.csr -config openssl-san.cnf
Above command generate a Certificate Signing Request (CSR) file with its key file by use of Certificate Template “openssl-san.cnf”, then follow a procedure to create a certificate file for website “apache1” with active directory certificate service as we discuss above.
Installation and Configuration of Apache Web Server on RHEL 9/RHEL 8/RHEL 7/CentOS 8/CentOS 7
Setup Apache Web Server Virtual Hosts on RHEL 9/RHEL 8/RHEL 7/CentOS 8/CentOS 7
Thanks for Read This Article



Comments
Post a Comment